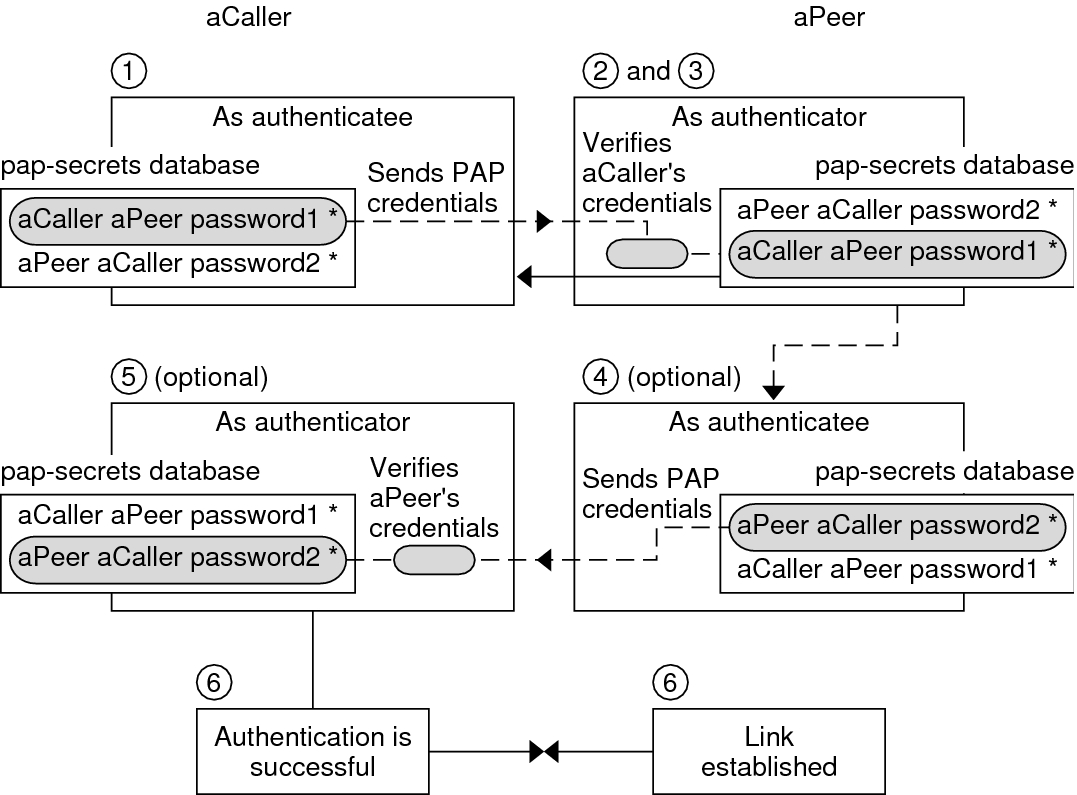
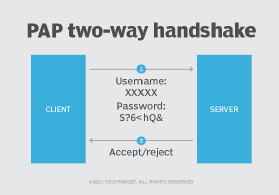
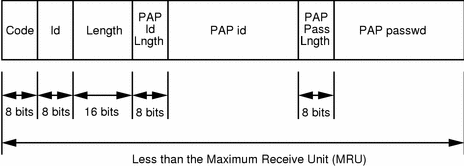
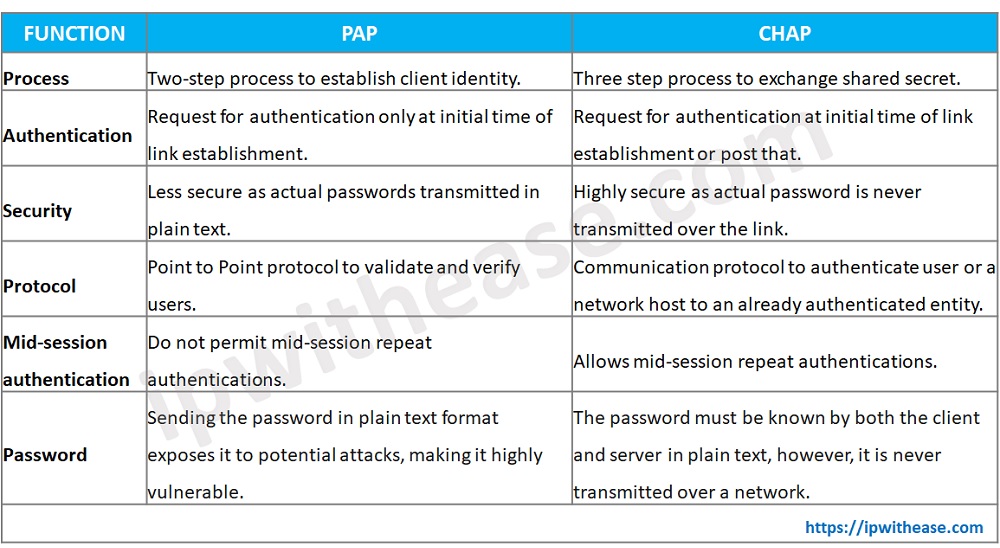
Pap Password Authentication Protocol Acronym Stock Illustration - Download Image Now - Acronym, Business, Computer - iStock
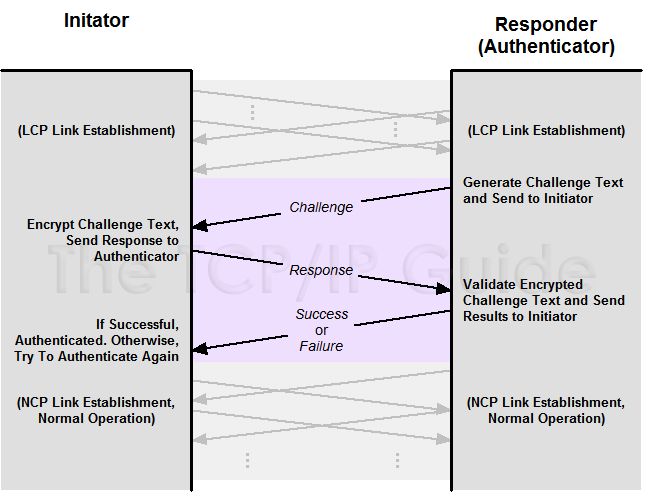
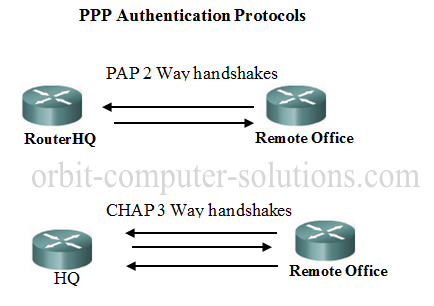
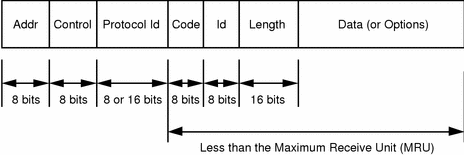
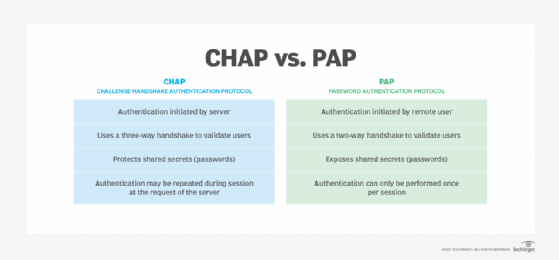
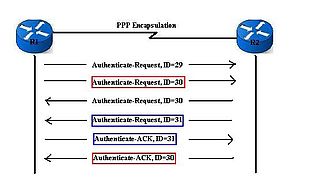
The TCP/IP Guide - PPP Authentication Protocols: Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP)
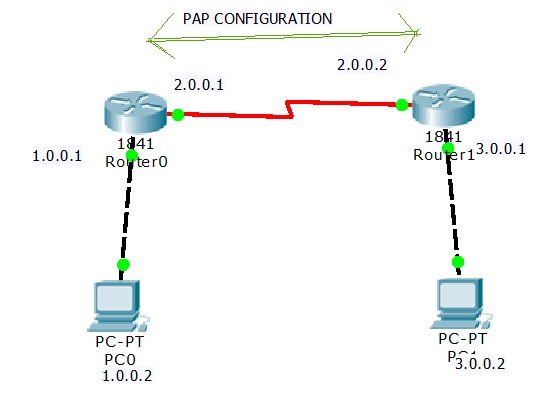
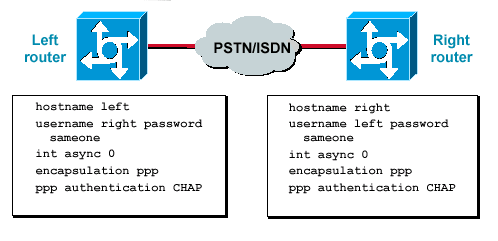
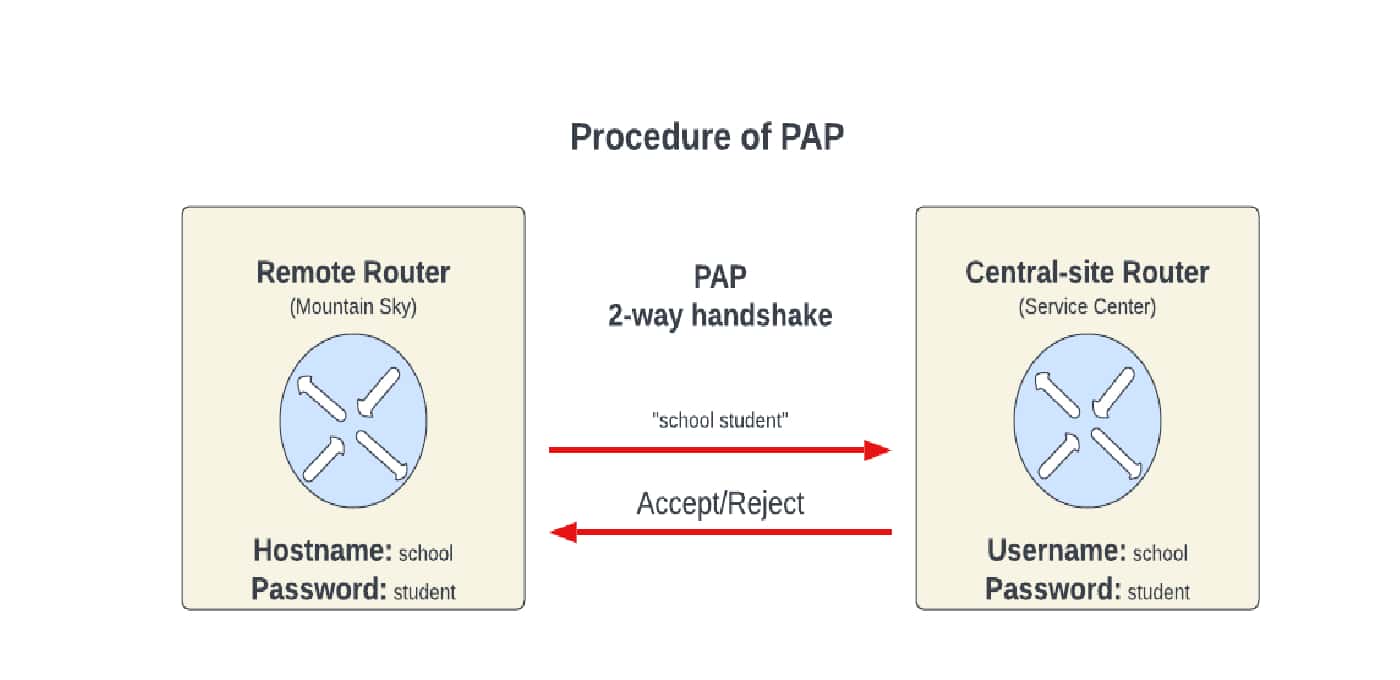
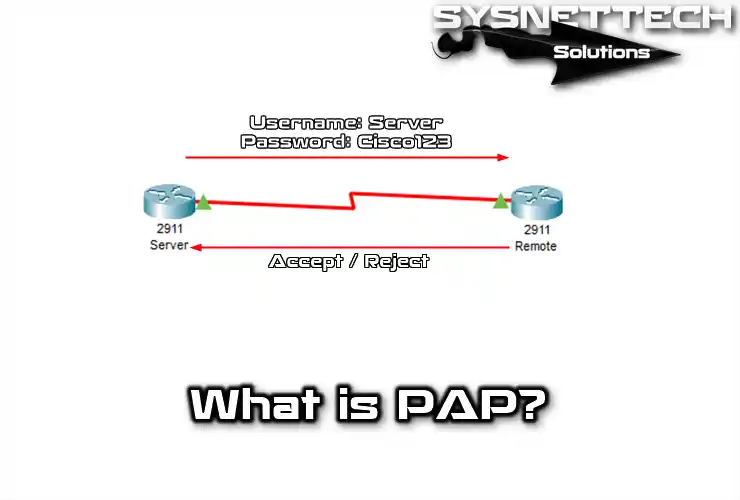
PAP(Password Authentical Protocol) Configuration on cisco router – Learn Linux CCNA CCNP CEH CISSP CISA Penetration-Testing Bug Bounty IPv6 Cyber-Security Network-Security Online